Today’s lesson goal: Understand the technical details of the TLS handshake process, ensuring secure internet communications.
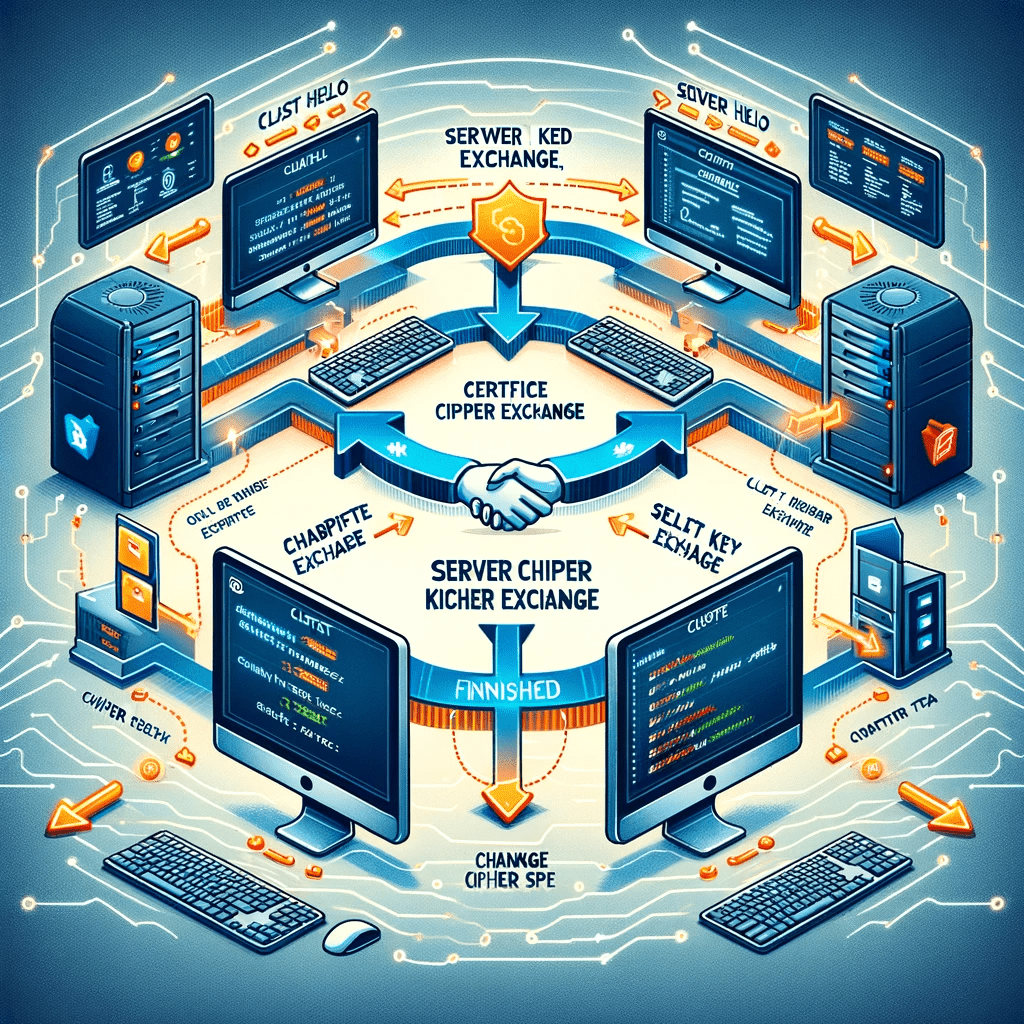
The TLS (Transport Layer Security) handshake is a critical process used in securing internet communications. It involves the negotiation of security parameters between two parties – typically a client and a server – before the actual transfer of data.
1. Beginning the Handshake:
- Client Hello: The process begins with the client sending a “Client Hello” message. This message includes the client’s TLS version, a list of supported cipher suites (algorithms for encryption, key exchange, and authentication), and a random byte string used in subsequent cryptographic computations.
2. Server Response:
- Server Hello: The server responds with a “Server Hello” message, selecting the TLS version and cipher suite from the options provided by the client. It also sends its random byte string.
- Certificate: The server provides its digital certificate, which contains the server’s public key and is verified by a trusted certificate authority (CA).
- Server Key Exchange: If needed, depending on the chosen cipher suite, the server may send additional key exchange information.
- Server Hello Done: This message signifies the end of the server’s initial response.
3. Client’s Confirmation and Key Exchange:
- Client Key Exchange: The client, upon validating the server’s certificate, sends its key exchange information, which includes a pre-master secret encrypted with the server’s public key.
- Certificate Verify: If client authentication is required, the client also sends a digitally-signed certificate.
4. Finalizing the Handshake:
- Both parties generate a master secret from the pre-master secret and their respective random byte strings.
- Change Cipher Spec: Both client and server send a “Change Cipher Spec” message, indicating that subsequent messages will be encrypted.
- Finished: Both parties exchange encrypted “Finished” messages, verifying that the handshake occurred without tampering.
5. Secure Communication:
- Following the successful handshake, data transfer begins, with all information encrypted using the agreed-upon cipher suite.
This process ensures confidentiality, integrity, and authentication in communications over the internet.
For a visual demonstration, check out this YouTube video: TLS Handshake Explained.
Since the request does not require an image for this lesson, let’s move on to the resources for further reading and exploration:
(c) 2014 Knowledge-Brothers.com – V00.01